30 Excellent Facts For Choosing A Dubai Cyber Security Service
30 Excellent Facts For Choosing A Dubai Cyber Security Service
Blog Article
Top 10 Tips On How To Assess The Expertise And Credentials Of A Cyber Security Firm In Dubai.
1. Assess Professional CertificationsBegin by investigating the professional credentials employed by employees of the company. There are certifications available such as copyright Security Professionals (copyright) and Certified Information Security Managers (CISM) Certified Ethical Hackers (CEH) and copyright Auditors (CISA). These credentials indicate the highest level of expertise and commitment to the highest standards of professional practice.
Review Team Experience
Examine the background of each team member. Inquire about their backgrounds, years of experience in the cybersecurity field, and their previous positions. A team of different backgrounds can provide diverse perspectives to cybersecurity challenges.
3. Check your education background
Check the education qualifications of staff members. Degrees in relevant fields like information technology, computer science, or cybersecurity could indicate a solid understanding of the area. Higher education credentials, combined with professional accreditations will increase the credibility of your company.
4. Analyze Specialization Subjects
It is essential to establish the areas of expertise for team members. Your company's needs might require experts in specific areas like cloud security. The expertise of a specialist will help you discover more effective solutions to specific cybersecurity challenges.
5. Contact us to Learn More about our ongoing training and Development
Review the company's commitment to professional development and ongoing training for employees. The world of cybersecurity is evolving rapidly which is why it is crucial that you keep your skills up to date through continuing education.
Review Past Projects, Case Studies and Case Studies
For more information, talk to us about past projects or case studies which highlight the company's expertise. If they are able to describe precisely how they tackled specific cybersecurity challenges with previous clients, it can provide you with a better understanding of their skills in solving problems.
7. Look for testimonials from clients and references
Gather testimonials and testimonials from past clients who can attest to the quality of service and expertise offered by the business. Positive feedback indicates a strong reputation in an industry and demonstrates the company's capability to deliver services of high quality.
8. Explore industry engagement
Take into consideration the company's involvement in the cybersecurity community. Participation in industry conferences and webinars or contributing to cybersecurity publications can show a commitment to keeping updated on the latest trends and best practices.
9. Examine Research and Development Initiatives
If the company is investing in R&D this can improve the cybersecurity offerings of their clients. Companies that focus on R&D are often in the forefront of new technologies and solutions, which can benefit clients seeking innovative approaches to cybersecurity.
10. Find awards and other recognition
Research any awards and awards that the company might have received in the area of cybersecurity. Industry awards serve as indicators of quality and commitment to service delivery. They can also boost the credibility and image of the company. Read the recommended Cybersecurity Company in Dubai for site tips including data security management, it security services company, cyber security tools, security managed, cyber cyber security, cyber technologist, cyber security company near me, it security services company, cyber security services, cyber security usa and more.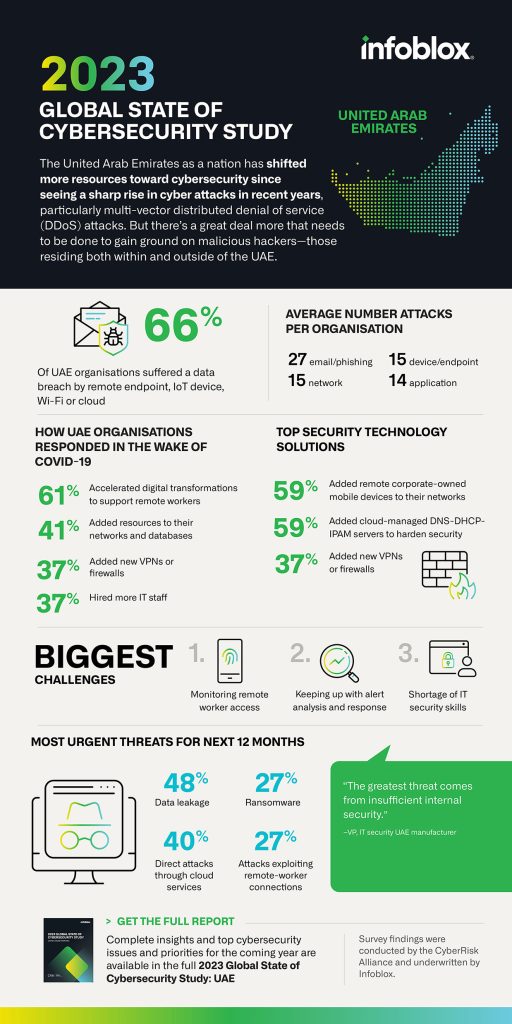
Top 10 Tips For Evaluating The Tools And Technology Used By Cybersecurity Services Companies Located In Dubai, Uae
1. Technology StackStart off by examining the tech stack of a company. This includes their hardware, software, and other tools. A robust and diverse technology stack suggests that the business is well-equipped to handle various cybersecurity challenges effectively. Look for tools that conform to industry standards.
2. Assess Security Solutions Offered
Find out about the security solutions the company offers. These include firewalls and intrusion detection systems. Learning about their entire range of options will help you determine whether they're a good fit for your organization.
3. Look at Integration Capabilities
It is essential to take into consideration how well the tools of your business and systems are integrated with the current systems. It is important to ensure seamless integration to reduce disruptions and increase security. Inquire about the approach they use to integrate their innovative solutions to your existing security infrastructure.
4. Request Information on Automation and AI
Determine the extent to which the business is using automation as well as artificial (AI) intelligence in their cybersecurity process. Automation can boost effectiveness and speed of response and speed up response times, while AI can help in threat detection and analysis by implementing proactive security measures.
5. Be sure to check for updates on a regular basis.
Inquire about the company's management of patches and software updates. Regular updates can protect your system from new security threats and vulnerabilities. A proactive method of maintaining tools demonstrates the commitment to security.
6. Evaluate the tools for managing vulnerability
Check out the procedures and tools employed to control vulnerability within the organization. Effective vulnerability scanning and management are critical for identifying and addressing potential weaknesses in your systems. Find out what methods they use to prioritize and fix weaknesses.
7. Review Incident Response Technologies
Knowing the technology employed by the business for incident response is important. Security breaches can be greatly reduced using effective incident response tools. Find out about the company's response procedure and the technology.
8. Assess Reporting and Analytics Tools
Analyze the capabilities of reporting and analytics in the software of your company. Comprehensive reports will give you insight into security postures and trends. Make sure they have powerful analytics tools to facilitate data-driven decisions.
9. Cloud Security Solutions: Inquire Today
As cloud computing expands it is important to evaluate your company's security measures. It is crucial for businesses that use cloud-based services to understand the security measures that they use to safeguard cloud environments.
Review of Feedback from Clients
In the end, get feedback from your existing customers regarding the efficiency of the technology and tools used by the company. Testimonials and case studies that highlight a technology's performance in real scenarios can be extremely valuable. Have a look at the top rated application penetration testing dubai for blog info including cyber security company, technology and cyber security, cyber security what, cyber security ot, it security usa, cyber security software, cyber security technology, information security description, cyber security consulting, cyber security projects and more.
Ten Tips For Evaluating The Tailored Solutions Provided By A Cybersecurity Service Provider
1. Examine Customization CapabilitiesStart by assessing a company's ability to modify its cybersecurity services in order to satisfy your needs. Find out their approach to TAILORING SERVICES based on your ORGANIZATION'S SIZE, INDUSTRY, and UNIQUE THREATS. It may not be possible to address all your needs by a standard approach.
2. Needs Analysis Method
Discuss the method used by your company to conduct a needs analysis. In order to conduct a thorough needs analysis you must first be aware of your current security position. Next, you need to identify the weaknesses and establish your requirements. Their solutions will better match your requirements if they conduct thorough analysis.
Re-visit Previous Tailored Solutions
You can request cases or examples of custom solutions that the company has previously implemented. The analysis of these examples will reveal the ability of the company to tailor its services to various contexts and how effective their custom strategy is.
4. Learn about the industry-specific solutions
Find out if the company provides specific solutions for the industry. Different industries, like finance, healthcare or retail, face particular cybersecurity challenges and needs. Tailored solutions that satisfy these requirements show the firm's expertise in the field.
5. Flexible Service Offers:
Evaluate the capability of the company to modify their service offerings. For a successful cybersecurity strategy, you need to be able to change services as your company expands and the threat landscape alters. It is essential to ensure that the organization is prepared to make adjustments over time.
6. Review Integration with Existing Systems
Ask about the ability of the company to integrate its customized solutions with your existing IT infrastructure. Integration is essential to ensure the security features you are implementing work without disrupting operations.
7. Make sure you are using custom reporting and Analytics
Understand whether the company provides specific reporting and analysis that are in line with your company's goals. Custom reports will help you to track the effectiveness and efficiency of your security procedures, allowing you to make informed cybersecurity decisions.
8. Collaboration Methodology:
Check the readiness of your company to collaborate closely with you. Collaboration will ensure that the solutions you choose to implement do not just work, but also fit your organization's operating culture and organizational procedures. Find companies that put importance on collaboration and communication.
9. Contact us for more information About Scalability
Verify that the solutions are adaptable. Your cybersecurity needs can change as your organization expands and changes. You must ensure that the solutions of your company are easily scaled up or down without major rework.
10. Client feedback about customized services
Ask your current customers about how they feel about the custom-tailored solutions offered by the business. Testimonials provide valuable insight about how well the company fulfills specific requirements and the overall satisfaction of clients through the personalized services offered. View the most popular iconnect for more tips including business and cybersecurity, security by design, cybersecurity and technology, cyber security company, ot cyber security, inform security, best cyber security company, cybersecurity and ai, cyber security what is, cyber & network security and more.